They finally did it.
-
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
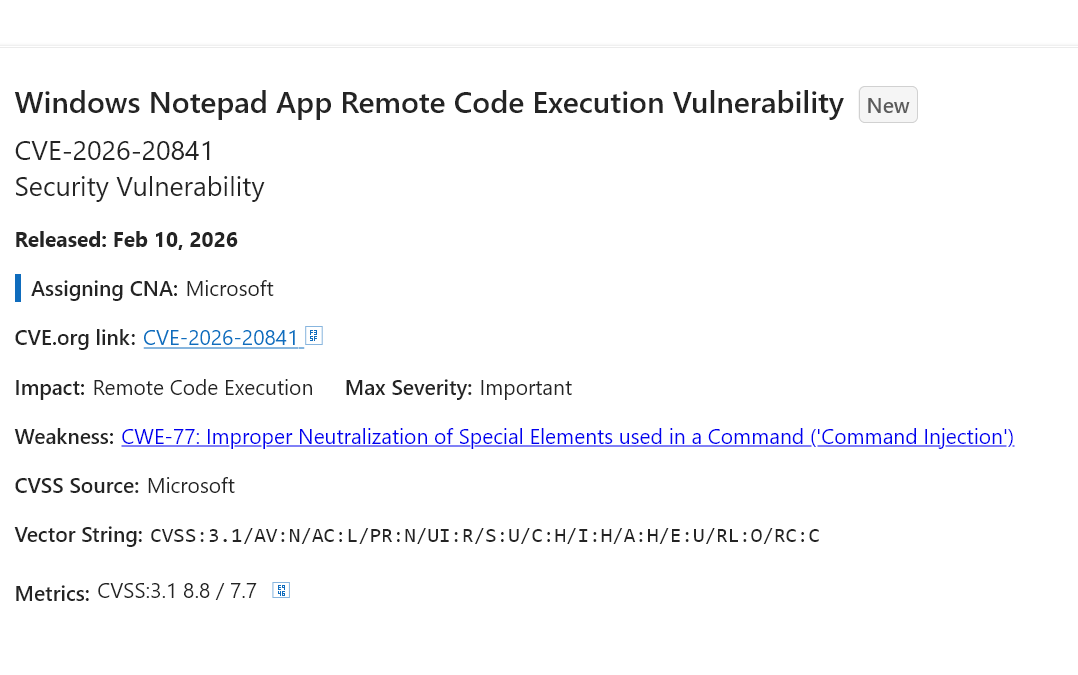
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore?

#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology
@pheonix You have to click a link. Merely opening the file isn't enough if I'm reading it correctly. That makes it comparable to Internet Explorer back when it would happily download and run any .exe. So pretty stupid.
-
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore?

#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology

@pheonix Given that WordPad had that built in, and MS killed it; not surprised
-
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore?

#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology

@pheonix and I still think they should have left support for formatted t3xt where it belongs, in Wordpad
Notepad could use syntax highlighting & auto-completion maybe ... -
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore?

#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology

@pheonix Windows 11 =
 ️
️ -
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore?

#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology

@pheonix @duniamelayu Linux?
-
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore?

#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology

@pheonix Don’t forget that Notepad++ was compromised recently too by state actors… https://notepad-plus-plus.org/news/hijacked-incident-info-update/
-
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore?

#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology

@pheonix I believe nothing has ever been safe
 The only state that approaches it is "not compromized yet"
The only state that approaches it is "not compromized yet" 
-
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore?

#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology

-
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore?

#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology

-
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore?

#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology

@pheonix Valt het jullie ook op dat een klaarstaande Windows-update de werking van applicaties beïnvloedt? Als programma's op een vreemde manier reageren en het icoontje "afsluiten en updaten" is zichtbaar, weet ik al weer hoe laat het is. Na updaten en herstarten werkt het dan weer normaal.
-
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore?

#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology

@pheonix another reason to switch on linux, only thing that can hold someone from switching is adobe software
-
@jkb @pheonix That seems to be the case, although the weakness is in Microsoft Notepad incorrectly handling “an unverified protocol”, not in something the user then has to do or interact with. Besides clicking a link.
This reads to me like an URI protocol handling issue.
And that functionality is not something they’d have to reinvent or vibe code.
You know, with their proprietary plain text editor running on their proprietary OS, and next to their proprietary file explorer, their proprietary internet browser, their proprietary email client and proprietary network agents.
All their proprietary software handling URI protocols… RIGHT THERE.
@avuko @pheonix Yes, indeed. And yes indeed this is something that should have never happened, the whole situation is shameful.
I was just pointing out that this vulnerability requires additional user input (albeit a very likely user input that normally shouldn't raise any concern), it's not one of those nightmare situations in which the mere opening of a file triggers an exploit.

